How to Deposit Money into ATMs Known as Scum: A Step-by-Step Guide to Safe and Legal Access
How to Deposit Money into ATMs Known as Scum: A Step-by-Step Guide to Safe and Legal Access
In a striking blend of financial innovation and caution, understanding how to deposit money into ATMs marked as “scum” demands both clarity and vigilance. These ATMs—often linked to decommissioned accounts, suspicious RAM storage, or fraudulent instrument swipes—operate outside mainstream banking oversight. While the term “scum” evokes risk, operating within legal frameworks allows users to engage safely and recover lost liquidity.
This guide explores verified methods, critical insights, and best practices to deposit funds responsibly into such environments, empowering users to navigate this gray zone with confidence and caution.
Atm scum devices are not standard retail ATMs; they function through clandestine setups that intercept unsecured transactions—either through stolen strips, cloned cards, or compromised physical points of sale. Unlike regulated machines, these scum machines lack banking SSL encryption and transaction safeguards, increasing exposure to fraud.
Their presence fluctuates but remains a persistent challenge in underbanked or high-fraud regions. Where traditional ATMs require card insertion and PIN entry, scum devices often use imaging techniques or direct file insertions to capture card data and payload amounts, bypassing conventional security checks. Legal recruitment through these channels is rare and typically tied to compliant cryptocurrency exchanges or authorized brokers—never unlicensed operators.
Understanding the Risks Behind Scum ATMs
Deploying funds at a known scum ATM carries significant financial and legal implications. These devices operate outside regulated banking systems, meaning transaction reversals are nearly impossible, and chargebacks do not apply. Users often face irreversible losses if skimming inserts or malicious firmware alter the fund-handling process.“Law enforcement regularly identifies scum ATMs in transient zones—former hardware stores, shuttered kiosks, or repurposed kiosks,”
says Anita Torres, a financial crimes analyst. “Victims typically swap a legitimate card for a counterfeit copy or upload data to a malicious chip, enabling silent fund drains.”
Risks include: - Immediate unauthorized asset depletion; no withdrawal protection - Exposure to third-party scammers—even if the machine appears functional - Blacklisted transaction flags that disrupt future banking access - Potential complicity in money laundering if funds originate from illicit activity Financial institutions warn that depositing into unregulated ATMs compromises consumer safeguards, leaving users without recourse if stolen card data surfaces post-transaction.
Legal and Secure Deposit Methods into Scum ATMs
Proceeding into a scum ATM requires strict adherence to regulated protocols.Users must identify and engage only with brokers, exchanges, or service providers operating under formal oversight. Reputable platforms vet locations, install tamper-proof hardware, and implement multi-layered transaction logging—features absent in unauthorized scum setups. Even in high-risk environments, compliance remains the cornerstone of security:
Only engage ATMs affiliated with licensed cryptocurrency brokers or regulated forex services, where deposit instructions are transparent and encrypted.
Avoid unbranded kiosks, repurposed security deposit boxes, or ADPs (Automated Deposit Points) with odd markings. Verify visibility of EMV-compliant readers and active security indicators—LED blinks, transaction disclosures, or secure communication lights. A key safeguard is partnering with intermediaries who operate within legal boundaries: - Cryptocurrency on-ramps using KYC-verified customer onboarding - Licensed remittance services embedded with audit trails - Authorized fintech platforms integrating biometric verification and real-time monitoring Always confirm the machine’s registration status through official databases such as FinCEN’s SAR filings or national banking authorities.
Avoid sham transactions disguised as deposits—red flags include missing security seals, uncharacteristic software, or inconsistent physical construction.
Step-by-Step: The Safe Deposit Process
Executing a deposit into a scum ATM demands precise coordination and awareness. Follow this structured approach to minimize exposure and maximize control:Step 1: Pre-Deposit Research - Validate the operator’s credentials using public registries: check for licensing numbers, SWIFT identifiers, or exchange affiliations.
- Review online feedback and security reports from financial watchdogs to detect recurring scam patterns. - Confirm that the machine displays a tamper-evident case and valid POS lighting; reject opaque or damaged units outright. Step 2: Site Preparation - Approach cautiously—scum ATMs are often unmarked or disguised.
Inspect surroundings for hidden cameras, cloning tools, or tampering signs. - Bring only essential items: the target card, ID, mobile device for live monitoring, and a secure wallet to store unused cash. - Use a dedicated deposit device if available—some brokers deploy shielded inserters to reduce skimming risk.
Step 3: Device Initialization - Perform a physical security sweep—verify integrity of rollers, slip guards, and firmware signatures. Any deviation triggers immediate cancellation. - Power on the terminal and confirm authentication medium compatibility (NFC, chip, or physical card).
- Initiate transaction workflow using only pre-approved software; disable external connections to prevent malware injection. Step 4: Transaction Execution - Scan card QR or insert discreetly; verify device prompts for transaction details—amount, sender, timestamp—before confirmation. - Cross-check displayed figures with printed confirmation—no electronic noise or verbal prompts.
- Leave immediate feedback loop: use a static device (e.g., encrypted messaging app) to verify receipt. Reject silent or automated confirmations. Step 5: Post-Deposit Protocol - Withdraw funds within 2–4 minutes to prevent stale transaction tokens.
- Record all activity in a secure log—machine ID, timestamp, deposit amount, and recipient verification. - Triggers immediate reporting if discrepancies arise—contact broker’s embedded support hotline or regulatory channel without delay.
By formalizing each phase under regulated oversight, users retain audit trails and limit liability, even within uncertain environments.
Real-World Examples and Case Studies
A 2023 audit by the Europol Financial Intelligence Unit highlighted a high-profile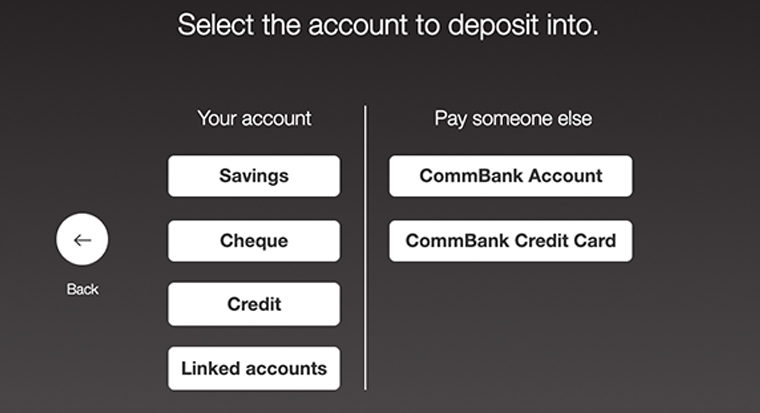


Related Post

Seamless Care, One Click Away: How EssSelfServiceNorthwell Transforms Patient Service Delivery

Exploring The Enigma Of Rumah Perjaka: A Cultural Journey Through Indonesia’s Hidden Heritage

Jual TONGKAT KAYU PRAMUKA 160 CM / TONGKAT PRAMUKA – Take Home Nature’s Warmth on Shopee Indonesia

Funeral Patrick Wayne Net Worth: What the Likeness Legacy Reveals

