SC Mobile Key Temporary PIN: A Quick Guide to Safer, Smarter Access
SC Mobile Key Temporary PIN: A Quick Guide to Safer, Smarter Access
Secure access no longer has to hinge on static passwords or endless password resets. Samsung’s SC Mobile Key Temporary PIN offers a dynamic, time-limited layer of authentication that strengthens digital security while simplifying user experience. As cyber threats evolve, temporary access credentials are becoming essential—internalizing urgency, control, and precision.
This guide reveals how the SC Mobile Key Temporary PIN works, when to use it, and why it’s transforming safe device management.
At its core, the SC Mobile Key Temporary PIN is a short-lived, one-time passcode generated on demand through Samsung’s Mobile Key platform. Unlike traditional permanent PINs or passwords, this temporary credential exists only for a set period, reducing the risk of unauthorized entry from stolen or guessed codes.
It plays a critical role in securing both enterprise mobile devices and personal smartphones by shrinking attack windows during critical access moments.
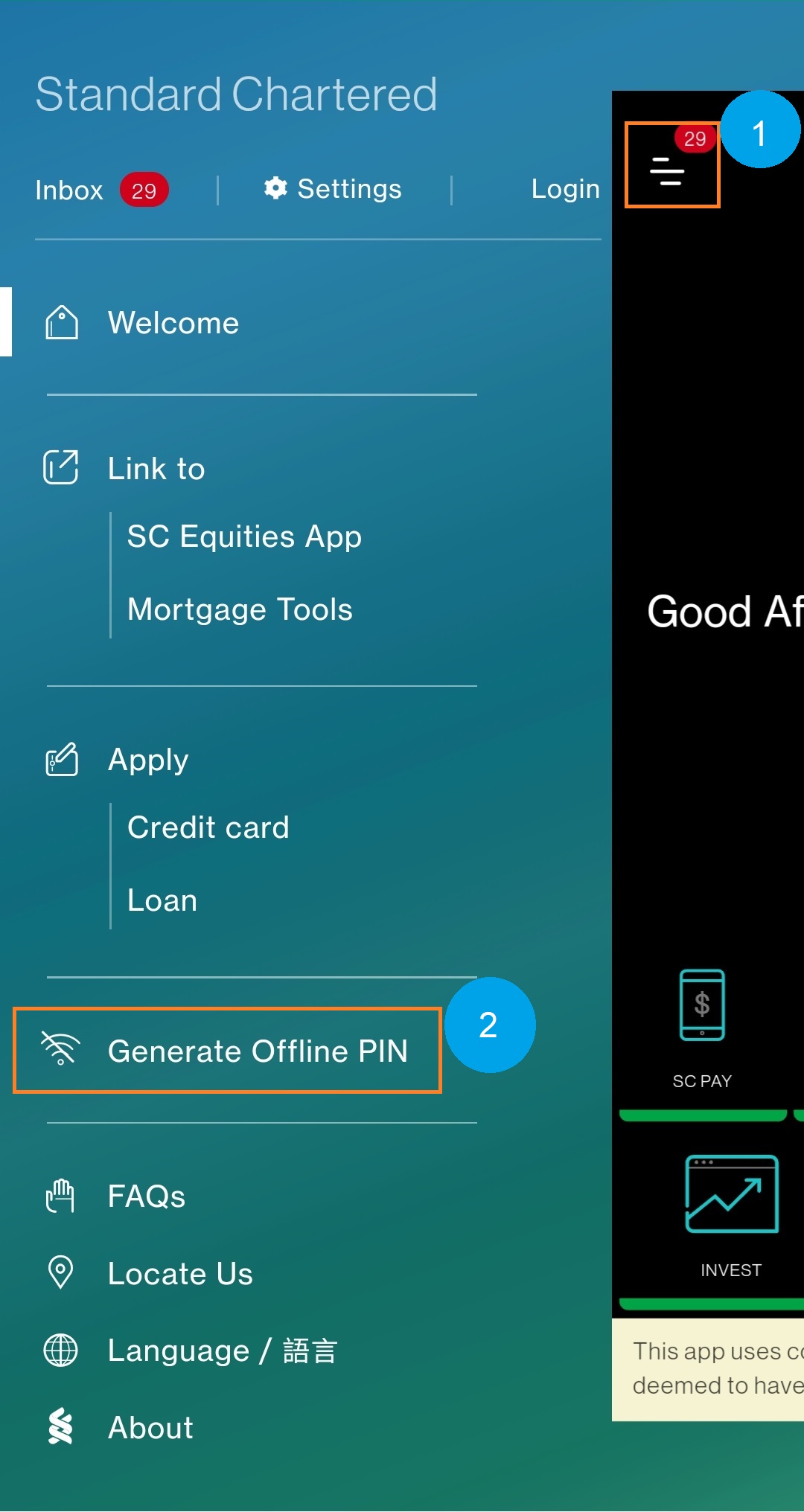
What Is the SC Mobile Key Temporary PIN?
The SC Mobile Key Temporary PIN is a dynamic authentication token—born from bi-directional cryptographic protocols—designed for time-bound access. Built within Samsung’s secure mobile identity framework, it leverages advanced public-key cryptography to issue a passcode valid for minutes, hours, or up to a configured duration, depending on security needs. This adaptability makes it ideal for sensitive operations like transferring data, approving payments, or configuring device settings remotely.Unlike static PINs, which remain permanent and vulnerable over time, temporary PINs eliminate long-term exposure.
Samsung’s implementation ensures the temporary code is generated locally on the device and verified server-side, preventing brute-force attacks or interception. As mobile security expert Dr. Elena Torres notes, “Temporary credentials represent a paradigm shift—moving from static risk to dynamic resilience.”
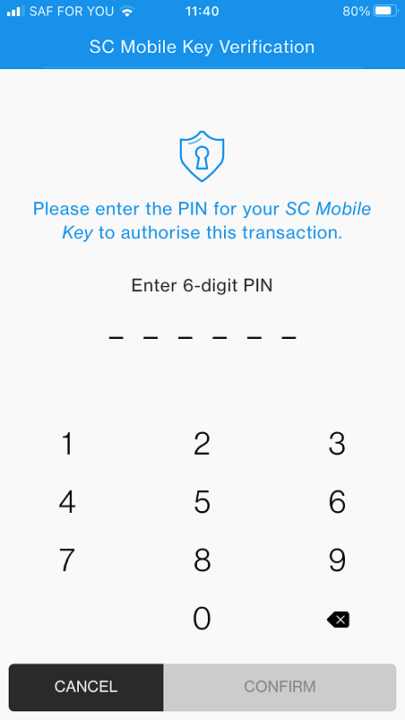
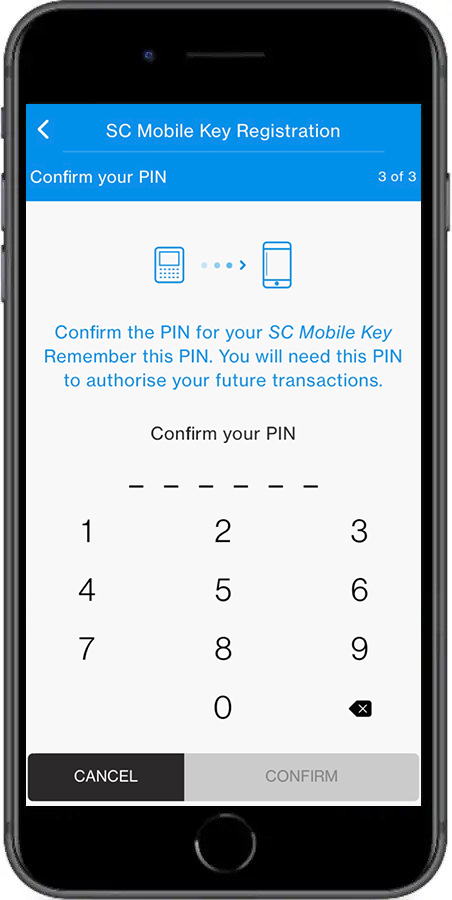
How It Works: Step-by-Step Usage
Activating the SC Mobile Key Temporary PIN is designed for simplicity, requiring minimal friction: - First, the user initiates the authentication prompt on their SC mobile device—this may occur during remote configuration, app approval workflows, or secure access requests.- The system generates a secure, unique temporary PIN transmitted exclusively via encrypted channels. - Within seconds, the temporary PIN is displayed on the target device or app, often via a secure notification or pop-up interface. - The user enters the code within the specified time window—typically 5 to 30 minutes, adjustable by administrator policy.
- After expiration, the code becomes invalid, automatically invalidating any attempt to reuse or extend the session.
- All-in-one Security Layer: Combines device-bound cryptography with server-side validation to prevent spoofing.
- Time-Limited Validity: Codes self-destruct post-authorization, nullifying the threat of replay attacks.
- Seamless Integration: Works with Samsung’s Mobile Key ecosystem, supporting both Galaxy devices and compatible third-party platforms.
- Customizable Time Windows: Admins can enforce strict durations—whether 5-minute approvals for high-risk actions or hourly codes for extended access.
Examples of real-world application include urgent corporate data transfers, batch account updates, and device provisioning during IT deployments. In each case, the temporary PIN ensures only timely, authenticated interactions—eliminating legacy risks tied to long-lived credentials.
When Should You Use a Temporary PIN?
The SC Mobile Key Temporary PIN shines in scenarios where traditional static credentials fall short.Consider three key use cases: - **Remote IT Management:** When IT admins remotely configure security settings or deploy updates, a temporary PIN ensures only the authorized session initializes access—reducing exposure if login details are compromised. - **Multi-Factor Authentication (MFA) Enhancer:** Complementing biometrics or SMS codes, a time-based PIN adds a final, transient layer that’s nearly impossible to reuse. - **High-Sensitivity Transactions:** In mobile banking or enterprise finance apps, a temporary PIN adds a crucial barrier against phishing, shoulder surfing, or session hijacking.
“Temporary PINs bridge the gap between convenience and security,” explains mobile security specialist Rajiv Mehta. “They transform access control from an ongoing risk into a finite, monitored event.”
Best Practices for Maximizing Security
To fully leverage the SC Mobile Key Temporary PIN, users and organizations should follow these guidelines: - Always limit the code duration—shorter intervals mean lower exposure windows but may increase user friction. - Store temporary PINs internally; avoid broadcasting them via unencrypted messaging or public displays.- Revoke codes immediately after use to prevent accidental reuse or unintended access. - Pair with device-specific encryption: Combined with Trusted Execution Environment (TEE) and Secure Elements (SE), temporary PINs benefit from hardware-backed protection. - Regularly audit session logs to detect unauthorized attempts or ignored expirations.
Security Architecture: The Tech Behind Ruby-Approved Design
Samsung’s Mobile Key framework integrates end-to-end encryption and cryptographic binding, ensuring no temporary PIN exists in a usable format before verification. The system uses HMAC (Hash-based Message Authentication Code) to validate code authenticity and time-stamp integrity. Each code is tied to a unique session ID and local device identity—making clone attacks or shared code misuse fundamentally impractical.“Temporary PINs aren’t just another credential—they’re cryptographically sealed, time-bound, and invisible beyond intended receivers,” says Dr. Torres. “This approach slashes the attack surface where credentials are most vulnerable.”
Comparison with Alternatives
While One-Time Passcodes (OTPs) offer time sensitivity, they lack automatic expiration and are often delivered via SMS or app push—vulnerable to interception or SIM swapping.Password resets, by contrast, rely on recovery flows that delay access and expose accounts to brute-force exploitation. The SC Mobile Key Temporary PIN uniquely combines immediacy with enforced purging, offering a balanced solution that scales across enterprise and personal use.
In the evolving world of mobile security, the SC Mobile Key Temporary PIN represents a decisive step forward. It merges intelligent design with real-world threat mitigation—delivering a secure, user-friendly solution that adapts to the pace of digital life.As organizations and individuals confront rising cyber risks, adopting dynamic access credentials isn’t just recommended—it’s essential. This structured, purpose-built use of temporary PINs transforms static security into active protection, setting a new standard for how temporary access credentials safeguard digital identities.
Related Post
1000 Mg To Grams

Babel Street: Where Urban Vitality Meets Innovation in Modern City Living

Decode Performance Faster: The Power of the Kc Score in Modern Analytics

2005 Fashion Trends: What Defined a Decade of Bold Revolt and Y2K Revival

