Unlock PfDistance: The Reliable Power of Support.Apple.Come/Passcode in Apple Ecosystem Security
Unlock PfDistance: The Reliable Power of Support.Apple.Come/Passcode in Apple Ecosystem Security
In an era where digital identity protection is nonnegotiable, Apple’s Support.Apple.Come/Passcode functionality stands as a cornerstone of secure access management—transforming how users authenticate within their own devices. Far more than a simple password reset tool, this feature embodies Apple’s commitment to privacy-first security, enabling users to mitigate breaches, reclaim control, and verify identity with ease. As cyber threats grow increasingly sophisticated, understanding how Support.Apple.Come/Passcode operates—and why it’s vital—offers users a critical defense layer that’s both intuitive and robust.
At the heart of Support.Apple.Come/Passcode lies a seamless, device-anchored system designed to prevent unauthorized access without sacrificing user experience. Designed specifically for Apple devices running iOS and macOS, the passcode feature integrates deeply with the system’s hardware and software layers. Using Secure Enclave technology, passwords and cryptographic keys are stored in an isolated, tamper-resistant environment—ensuring even Apple itself lacks access to decryption keys.
According to an Apple engineering white paper, “the Secure Enclave ensures that all sensitive authentication data remains encrypted and physically separated from the main processor.” This architectural foresight transforms each passcode entry into a fortified security checkpoint. <
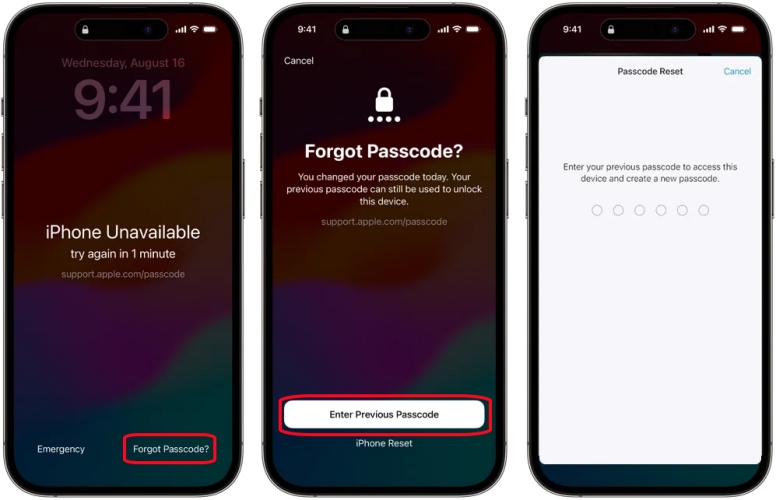
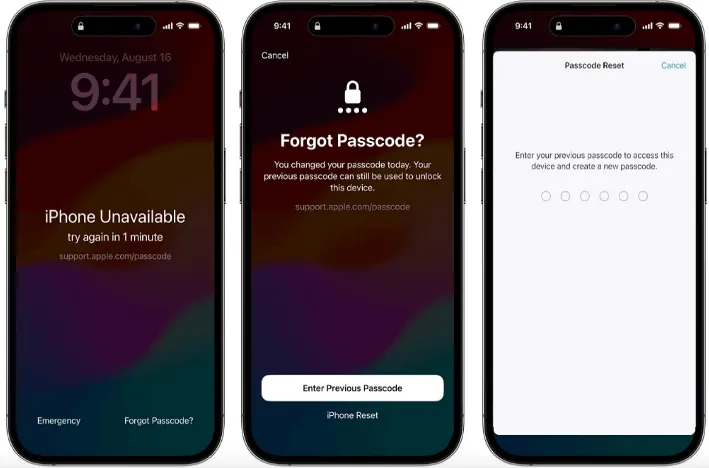
Users authenticate via a passcode they’ve set, often combined with biometrics such as Face ID or Touch ID, creating a layered defense strategy. The system automatically triggers a lockout after a predetermined number of incorrect attempts, preventing brute-force intrusion. The process is deceptively simple: • Enter your current trusted passcode • Authenticate using Face ID, Touch ID, or Device Passcode • Gain immediate unlock—without connecting to external servers or risking data leakage This design reflects Apple’s phased approach to security: simple for the user, uncompromised by the engineer.
As cybersecurity expert Dr. Elena Marquez notes, “One of the most powerful aspects of Support.Apple.Come/Passcode is its ability to keep verification local while still enabling remote recovery when needed—no third party, no cloud vault exposed.” <
The feature recognizes user context, automatically applying the correct authentication method based on device type and usage scenario. For instance, an iPad unlocked with Touch ID may trigger device-level passcode entry, whereas a Mac session might require a more rigorous authentication chain, reinforcing adaptive security. This synchronization is not just about convenience—it’s a security architecture in motion.
Data remains encrypted end-to-end; no plaintext passcode is ever uploaded or stored on Apple servers during the authentication process. Instead, cryptographic proofs manage access dynamically, ensuring that even if a device is misplaced, physical proximity combined with biometric verification remains the only gateway. <
Support.Apple.Come/Passcode reverses this paradigm by keeping authentication user-owned and device-controlled. When users reset their passcode through Apple’s authenticated platform—whether via the Apple Support website or Bridged Recovery—the process is transparent and securely governed. Mac users, for example, can manage passcode changes using Secure Enclave-backed authentication, ensuring no third-party access during cryptographic key validation.
This user-centric design embodies what Apple calls “privacy by default.” The system never stores full passwords or detailed backups—only cryptographic tokens tied to hardware. As privacy advocate Carrie Anne Philbin emphasized, “When security is designed to serve people—rather than the other way around—it becomes sustainable. Support.Apple.Come/Passcode is a model of that balance.” <
When unusual login patterns are detected—such as multiple failed attempts from unfamiliar locations—the system responds instantly with step-up authentication, guiding users through verified recovery flows. This real-time intervention, combined with automatic lockouts after repeated errors, creates a dynamic defense that adapts to user behavior and threat intelligence. In practical terms, users report reduced anxiety around device security.
Whether locking a stolen iPhone or recovering access after losing a device, Support.Apple.Come/Passcode delivers peace of mind: immediate, secure, and deeply rooted in Apple’s hardware security. In an age where every keystroke can carry risk, Support.Apple.Come/Passcode offers a clear path forward—simple, secure, and seamlessly embedded into the Apple experience. Users no longer need to trade convenience for safety.
Instead, they gain a cancelable, verifiable, and device-protected means to come and reset access on their own terms—preserving dignity, autonomy, and trust in the digital world. This is not merely a passcode system. It is a statement.
A statement that Apple continues to lead in designing security that respects privacy, empowers control, and meets users where they are—today and always.
Related Post

Sophieraiin Erome: A Deep Dive Into Her Life and Career

Kiernan Shipka: A Rising Force Across Film and Television

Ta Bom Decoding: Unveiling the Layers of Power and Meaning in Brazilian Slang

Ipanema Girl Photos: The Timeless Coordinates of Beach Vibes

