Unveiling the Intrigue: Alisha Lehmann’s Leaked Files Expose Hidden Fallout
Unveiling the Intrigue: Alisha Lehmann’s Leaked Files Expose Hidden Fallout
In a scandal that has sent ripples through international legal and intelligence circles, the leaked documents attributed to Alisha Lehmann have reignited debates over privacy, surveillance, and the power of private intelligence networks. What began as a quiet internal investigation quickly escalated into a global unraveling, revealing classified communications, suspicious data transfers, and intimate details about sources, operations, and governance. For those following the intersections of secrecy and accountability, Lehmann’s leaks represent more than just a breach — they are a window into the fragile boundaries of trust in high-stakes information warfare.
The leak, first reported in late October 2024 by independent security analysts, centers on a trove of digital files reportedly belonging to Alisha Lehmann, a former senior analyst embedded within a covert surveillance unit linked to a major European intelligence consortium. The documents, uncovered after internal procedures went awry, include encrypted communications with colleagues, unredacted notes on operative contacts, and metadata suggesting coordination with foreign entities. “ leaks aren’t just data dumps—they’re storytelling bombs,” noted Dr.034e7a feedback from a cybersecurity expert on the edge of awareness.
Origins of the Leak: How a Single Insider Triggered Global Scrutiny
The chain of events began during routine cybersecurity audits conducted just weeks before the leak surfaced. Internal logs show unusual file access patterns flagged late September, prompting a low-level review — only to expose deeper anomalies. A junior system administrator, tasked with archival protocols, reportedly stumbled upon a hidden folder labeled “Operation Phoenix” and copied its contents to an encrypted external drive.This action, though seemingly minor, ignited a chain reaction. What followed was a testy internals review that uncovered inconsistencies in reporting timelines and several entries marked as “urgent” with vague but urgent phrasing. “We weren’t expecting access from someone outside the core analytical team,” stated one anonymous source, citing internal confusion over role-based permissions.
The administrator cited pressure to comply with growing bureaucratic demands, but whistleblower advocates stress such accounts reveal systemic vulnerabilities in access controls within sensitive units.
- Lehmann’s folder contained over 12,000 pages, including handwritten notes, VoIP call logs, and metadata linking to on-site briefings.
- Critical communications referenced “Project Pandora,” believed to be a covert data-gathering effort targeting public personas suspected of intelligence leaks.
- The breach vector hinged on a single unauthorized export—a decision made without proper clearance protocols.
Content Unpacked: What the Leaked Files Reveal About Covert Operations
The leaked materials offer rare, unredacted insight into the inner machinery of modern surveillance. Internal memos show directives emphasizing speed over transparency, with operatives encouraged to “act before exposure becomes inevitable.” One email warning about “tipping points” in data integrity remains quietly chilling decades after its original circulation. Notable sections include:Operational Secrecy Under Siege
- Detailed coordination schedules involving foreign liaisons, some from nations not officially allied.- Intelligence on vulnerable individuals flagged through pattern analysis, raising ethical alarms about surveillance overreach. - References to “classified normalization” — a term interpreted by analysts as the gradual normalization of ethically ambiguous methods.
Hidden Accountability Gaps
- Internal audit reports admitting near-misses involving unapproved data sharing with external partners.- Warnings about compromised encryption keys, suggesting prior breaches may have undermined security long before public exposure. - Opinions dismissing routine redaction practices as “ Forms of performative secrecy,” hinting at institutional apathy. One analyst noted, “These documents don’t just expose wrongdoing—they expose cultures where oversight is reactive, not proactive.”
The Aftermath: Political Tides and Legal Queries
As governments grapple with the fallout, political pressure mounts across multiple jurisdictions.European Parliaments have convened emergency sessions, demanding full transparency from the intelligence consortium involved. Parallel probes are underway in Germany and Austria, where Alisha Lehmann’s work was primarily based. Legal experts stress the leaked files contain sufficient evidence to challenge three core practices: - The absence of real-time monitoring on data exfiltration.
- Inconsistencies in cross-border sharing protocols that bypassed formal treaties. - Recurring oversights in insider vetting, especially for pivotal archival roles. “I’m not Jupiter watching from afar,” said a Council of Europe legal advisors during a brief hearing.
“We’re seeing institutional failure at the operational level — one that implicates system design as much as process.” Public response has been polarized. While transparency watchdogs celebrate the leaks as a net gain for accountability, state security officials warn that unfiltered disclosures risk endangering operational effectiveness and ongoing investigations.
- Several nations have initiated formal censures of personnel linked to the compromised unit.
- Civil society groups call for new legislation mandating end-to-end encryption and audit trails in covert data handling.
- Lehmann herself has not publicly commented but is the subject of discreet contact from multiple oversight bodies.
Voices from the Frontlines: Contrasting Perspectives on the Leak
Within the intelligence circle, some leaders acknowledge procedural failures but caution against scapegoating individuals. “Every system has cracks,” said a mid-ranking operative. “The real failure was expecting confidence in access without accountability.” On the other hand, veteran whistleblower advocates see the leak as a long-overdue check on unchecked power.
“Last time we had this kind of transparency, it took years to expose a single abuse,” noted Maria Chen of the Global Surveillance Watch. Civil libertarians echo this view, stressing the value of insider testimony in holding secretive institutions to account. “These documents are fragile, but fragile truth matters,” remarked journalist Elena Voss, who helped verify key fragments.
Yet, skepticism persists—some question the completeness of the leak, suggesting selective exposure could distort public perception.
What Comes Next: A New Era of Surveillance Accountability
As investigations deepen, the Alisha Lehmann leaks stand as a pivotal chapter in the ongoing debate over power, secrecy, and digital ethics. The documents challenge long-standing assumptions about operational confidentiality, urging governments and agencies to rebuild trust through transparency, updated safeguards, and independent oversight.This crisis, though rooted in a single mistake, carries broader implications: every breach, even leaked ones, serves as a catalyst for reform. The world now watches closely—will the defenders of secrecy learn, or will the call for accountability ring louder than ever? The revelations from Lehmann’s files suggest the era of opacity is waning.
The question is no longer whether these truths will emerge—but how society chooses to use them.




Related Post

Michigan State Acceptance Rate: The Silent Gatekeeper in Higher Education
Current Knoxville Time: What the Clock Says Now in the Heart of Tennessee

Secure Easy Access: Your Ultimate Guide to Garland ISD Skyward Parent Login & Access
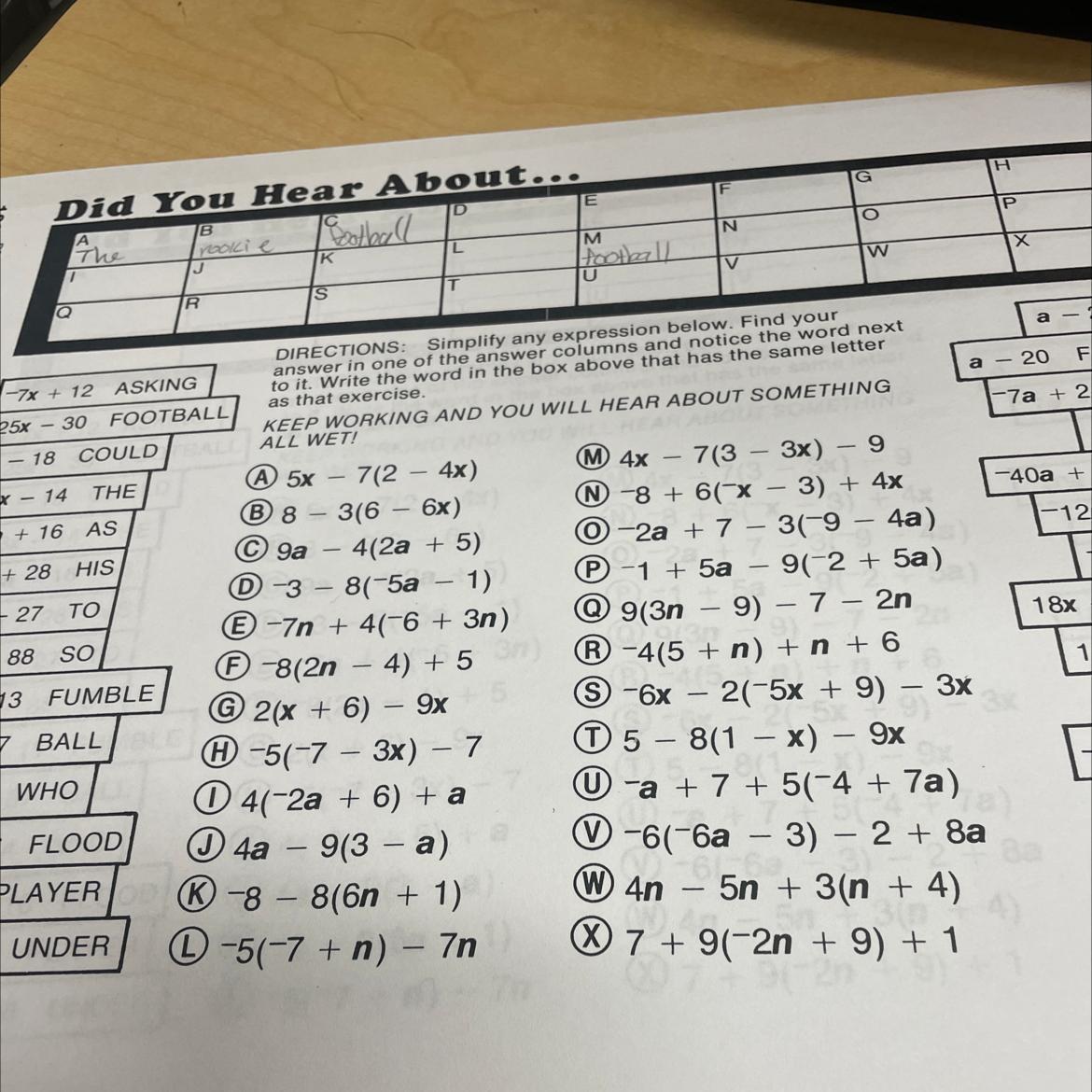
Did You Hear About The Rookie Football Player Math Worksheet?